 The release of the 3rd generation of the iPhone was the reason for me to rush to the TMobile store to get the 32G version. I had to wait for about one week first, but finaly got one, and I love it! But there is one thing that worries me a bit. I was able to remotely drain the battery in 30-45 minutes, just by pinging the public IP address, assigned by TMobile, to the GPRS/3G interface of the phone. Is your battery draining for no reason? Is your iPhone running hot when in standby modus? Then read on...
The release of the 3rd generation of the iPhone was the reason for me to rush to the TMobile store to get the 32G version. I had to wait for about one week first, but finaly got one, and I love it! But there is one thing that worries me a bit. I was able to remotely drain the battery in 30-45 minutes, just by pinging the public IP address, assigned by TMobile, to the GPRS/3G interface of the phone. Is your battery draining for no reason? Is your iPhone running hot when in standby modus? Then read on...
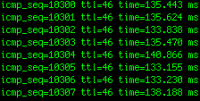
I was curious to see what IP address I was using during 3G networking. It turns out that on the Dutch TMobile network you are assigned a random IP within a block of TMobile mobile internet users. You can check this out by going to a site like whatsmyip.org, or installing the iStat app, which also shows you the 'cell IP' of the iPhone. To see if my iPhone was pingable, I issued the ping command on the OSX terminal on my MacBook, to which it responded. I was also be able use an app like Datacase, to share documents over the internet via FTP and HTTP from my iPhone. An Nmap to the device even reported that port 21 was open. Wtf? In other words, there is nothing between your device and the evil outside world when you switch on your iPhone, at least on the TMobile network in the Netherlands. Scary stuff.
When I was done experimenting, I noticed after 30 minutes that my fully charged iPhone ran a little hot and the battery suddenly was as good as empty, even though I had put it to rest by pressing the top button. It turned out that the ping I did half an hour before on my MacBook was still running and had kept the 3G module alive, sucking the energy from my phone. Crap!
I tried the same thing with a Nokia E71 on the same network, but this trick did not work. The E71 switches the 3G networking on when needed, for instance when the browser starts. Close the browser, and the device goes offline. I haven't tried other phones yet, but I'm curious to see how an Android reacts...
So, how could an attacker do harm to you and me remotely? Well, I used a nice tool called xprobe to do a remote ICMP fingerprint of the OS. One run of the tool against my public iPhone IP showed that the device was probably "Apple Mac OS X 10.3.x". Apparently, the iPhone responded with OSX characteristics. Easy catch! Someone can just scan the IP block with xprobe, and ping all iPhones he finds to death. Another, more targeted approach would be to lure you to his webserver, tailing and grepping his logs to see if any iPhones come along and then ping the device to death. He could also send you an email, containing a remote image to do this. Remote image loading is switched ON by default on the iPhone Mail app, so this method would be easier. Why would someone do this? For fun? An iPhone hater? Or just because?
Other networks in the Netherlands that offer GPRS/3G do not seem to be vulnerable to this problem because of the use of NAT or blocking inbound traffic. I hope that TMobile will do the same soon. Please share your experiences on other networks here.